Hackers and how they do it
Latest Hacks – How they Hack WordPress
A number of clients were hacked just before and after Easter. Some hosted with us, and some on other providers. We picked these up via our remote backup system and scans of the remote backups thanks to Blog Vault. This was a gravity forms vulnerability that the scum around the world have focused on recently.
This backup scans daily, and is a great way of doing it, as it creates no server load, and you can also compare file and system changes and additions and updates as well.
After informing a couple of hosts and clients who use there servers, they ran their usual server side scans, which we all rely on as a first pick up, or line of defence following a hack. Here is a classic example of a real clients site AFTER their server ran a threat scan and found NOTHING. Here is a live url on the site that anyone can access if they know the address. See what they can do? Upload any file they like to your website and then access it and run it… Criminal!
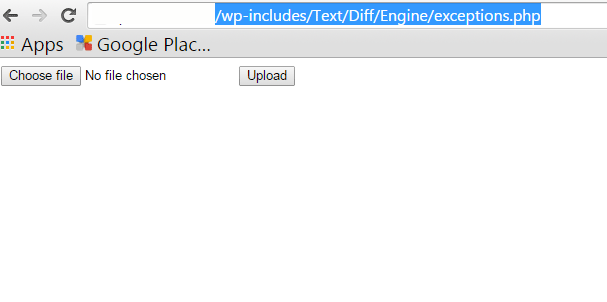
This is not malware, there is no malicious code per say, but, the ability is there to upload any file, program, action etc at any time. It is hidden as you can see from the url, 4 folders deep, and even looking for a time date stamp for changes will often hide the date until you dig down to the actual folder. Many times they are adding a few lines of code to an existing file to create this window, and you have to know code to see and read it, and then find and fix.
Then you have to shut down the vulnerability to your site, after you have examined the logs and found the entry point on the time date stamp. The real question is, should we leave this up and monitor and find them via the IP, and should we put some nice code on this page to give them an unpleasant surprise when they return to visit and blow up this site… Tempting, very very tempting.
Hosting is getting very serious, but hack removal is the best tool you can have…

